Just proving my credentials to be writing here.
Tonight as I walk down to my car I will have a laptop, an Ipaq, a 512Meg USB key and an iPod in my hands.

Just proving my credentials to be writing here.
Tonight as I walk down to my car I will have a laptop, an Ipaq, a 512Meg USB key and an iPod in my hands.
I find dictionary.com to be a very handy resource. But boy are their ads annoying. And it looks like they’ve gone that extra mile to get their popup ads to dodge around Firefox and IE+Google Toolbar’s popup defences. (At least I assume it’s them, not some other site with popups sitting in the background).
Not to mention the fact that the popup ads are the worst kind – the ones that look to people of limited computer-literacy like legitimate system messages, for instance:
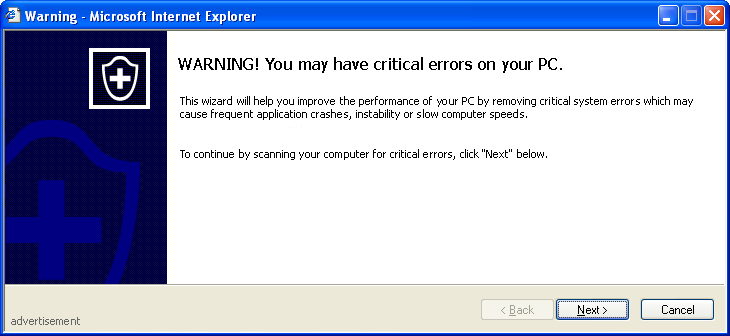
Oh sure, they have “advertisement” written in tiny tiny greyed writing in the corner. That makes it all better, doesn’t it. I wonder if Cancel actually closes it? (I clicked the X in the corner.)
I am unlikely to think you’re a legitimate software distributor if you say you’re selling “Microshit” software.
Hax0r gameshow contestant wagers $1337 on Jeopardy. (via Rick)
Gary Schare, Director of Windows Product Management at Microsoft, talks about the future of IE, its features and security. (Via Cameron Reilly)
Speaking of ADO (which I was yesterday), trying to figure out the black magic that is an OLEDB connection string? Try here.
Feel like writing a little C++ or Java applet for your phone? Here’s tech specs for Nokia phones. For me that’s the kind of project I’d love to do, but it will have to happen after I invent a time machine so I’ve got the time to do it in.
Where are we : ‘Internet’ or ‘internet’?
Every so often I’ll find the solution to an obscure issue, and wonder “why isn’t this in the MSKB? Why has nobody written an explanation I could find in Google?” Well through this site, now I can do something about that.
If you call an Access (Jet 4.0) query via ADO/MDAC, you may get empty recordsets back if the query uses parameters. There’s a bug that Microsoft reckons applies to RDO calls, but also appears to affect ADO/MDAC 2.7 in the same way.
To fix it you need to define the parameter size to an arbitrary amount before you set the parameter. Here’s some hopefully useful (to somebody, somewhere, some day) sample code…
(This is VB6. Dim everything beforehand of course, ‘cos everybody loves early-binding. What, you want to play with fire by using late-binding and no Option Explicit? Silly you.)
Set oCommand = New ADODB.Command
oCommand.ActiveConnection = gcDatabase.Connection
oCommand.CommandText = "select * from MyQuery"
Set oParam = New ADODB.Parameter
oParam.Size = 255 'Take this out and you get an empty recordset back, but no error. Wacky.
oParam.value = "your value"
oParam.Name = "your parameter name"
oParam.Type = adYourFieldType
oCommand.Parameters.Append oParam
Set oRS = New ADODB.Recordset
oRS.Open oCommand, adOpenForwardOnly, adLockReadOnly
(and close and destroy everything when you’re done, natch. You know what VB6’s garbage collection is like.)
We have a nice television, people often comment on it when they come to our house. They say things like “oooh, you have a nice television” and we say things like “thank you, we like it too”.
But of late I’ve been wondering why we have our nice television.
We spend most of our evenings on the net. I choose to listen to 6 Music (otherwise known as BBC 6) in preference to watching television in the evening. We read blogs, email friends, surf, download podcasts,study and work. Is this the way of the future? Will the internet kill the video star or are we abnormal?
What do you think?
FileZilla is my FTP client of choice. But it has one oddity: some files on the remote Unix system weren’t showing up — to be precise, .htaccess, which is pretty important in the web world, all things considered.
It occurred to me to check all the options to see if there was one that might be causing this. After all, a bug like that couldn’t continue to go unnoticed and unfixed, could it?
Sure enough… Edit -> Settings -> Interface settings -> Remote file list -> turn on “Always show hidden files”
Personally, I wouldn’t have made this the default, but then, there’d be a lot of things different if I ruled the world.
host gsmtp171.google.com[64.233.171.27] said: 552
5.7.0 Illegal Attachment (in reply to end of DATA command)
So, GMail bans zips and other archive files, at least if they contain executables. Seems to work if there’s no executable inside it.
Perhaps a reasonable precaution. A bit of a pain sometimes though.
Have a listen to this morning’s Radio National Background Briefing programme on nanotechnology. RealAudio or Windows Media. Interesting stuff.
Update 18/11: Transcript now available.
Today geekrant.org’s stylesheet was fading in and out of existance. Well, to be precise, the path to it got screwed up a bit, because somehow it thought it was in a directory called (deep breath):
http://www.geekrant.org/wp-login.php/wp-images/smilies/ wp-images/smilies/wp-images/smilies/wp-images/smilies/ wp-images/smilies/wp-images/smilies/wp-images/smilies/ wp-images/smilies/wp-images/smilies/wp-images/smilies/ wp-images/smilies/wp-images/smilies/wp-images/smilies/ wp-images/smilies/wp-images/smilies/wp-images/smilies/ wp-images/smilies/
rather than the much more succinct (and correct):
http://www.geekrant.org/
This appears to be caused by a bug in WordPress 1.21, where under some circumstances registered users go to login, and a particular browser/server configuration is present (looks like something to do with proxies) and it thinks the WordPress directory has moved, and tries to compensate. It’s detailed in the WordPress support forums, and if anybody’s having problems with it, the fix is to manually fix the siteurl setting in the wp_options table (it’s the first row) and to get into wp-login.php and comment out the two lines following
// If someone has moved WordPress let’s try to detect it
…because really, if someone’s moved it, they should have done it properly and updated the siteurl setting themselves.
See, not even WordPress is perfect. But it does have a strong user community, open source code that’s not too confusing to dabble in even for PHP-newbies like me, and a straightforward database structure holding all it’s stuff together. And that counts for a lot, I think.
I was asked to go step-by-step through how to protect WordPress from the current rash of spam comment attacks, so here it is. It’s fairly easy to get them to go into the moderation queue, but it’s a pain having to continually clear it out.
The way the current attacks (hold ’em poker and so on) are working is to attack a file called wp-comments-post.php which does the grunt-work of posting comments into the database… if this isn’t there, they can’t do it.
So first rename wp-comments-post.php to something else. Doesn’t really matter what, as long as it doesn’t clask with anything else. eg xyz.php. (It’s not ever seen by users so it really could be called anything without confusing people, though you might want to avoid confusing yourself if you later can’t remember what it is.)
Then you need to edit the files that call xyz.php, which are:
Save all those files to your server, and make sure the original wp-comments-post.php file is deleted, and then you should be done. Post a comment yourself to make sure it works.
For now it seems to stop the spammers… no doubt in future they’ll figure out something more advanced (like scanning the <form> code to figure out the name of the post file), but it should stop them for a little while at least.