It is a good idea to keep your computer systems up-to-date, by installing the latest software fixes. But there is one fix that Telstra needs to request and install, to fix a bug lurking on Telstra’s landline telephone system which scammers are making use of.
This is Part 4 of 4 of Scammers making use of Telstra landline bug.
- To learn about the scam, read Part 1
- to learn more about testing your landline and protecting yourself, read Part 2
- To find out how I became an unwitting victim 21 years ago, read Part 3.
Here, we explore some myths and facts about this bug, and I have some requests for information (please comment if you can answer any of the questions).
Facts and myths
- Fact:
- Scammers can intercept calls you make (shortly after they call you)
- Myth:
They’re intercepting all calls that everyone is making to 000, or the bank
The truth: there’s been a few crimes like this in the past (against radio stations), but not this time. Only one person’s calls get intercepted.- Fact:
- An evil caller can control your landline, preventing you from making calls, for up to five minutes.
- Myth:
Scammers can make calls to sex lines in Nigeria from your line
The truth: They cannot; if you see such calls on your bill, it was probably a family member or employee.- Fact:
- Scammers can imitate the bank’s phone menu (or they could make a temporary, actual connection which they cut off at the right time)
- Myth:
This bug enables them to fake my Caller ID
The truth: A separate hack applies to Caller ID, which the scammer might also use as part of their fraud.- Fact:
- An evil caller can prevent other callers from getting through to you (they get busy tone).
- Myth:
They can listen in on everyone who calls you
The truth: They have to physically wire a listening device across your line to do that. The method described here only allows a scammer to intercept calls you make, shortly after their call.- Fact:
- There is no indication if a call is still connected on the line after you hang up.
- Myth:
A scammer can be secretly connected to your line at any time
The truth: It doesn’t “just happen”. They have to call you first, and the effect only lasts for five minutes (maximum, in Australia).- Fact:
- Mechanical exchanges also had this characteristic
- Myth:
Every country operates like this
The truth: Only a few countries have this bug. New Zealand, Canada, the U.S., and many other countries do not have this bug. And mobile phone systems do not have this bug, either.- Fact:
- Various scams and tricks arising from this bug have been in use for some time. In the past, there was no five-minute timer, so it was possible to lock out someone’s line for weeks. Journalists and reporters, having interviewed someone for a story, would leave the call open preventing competeting journalists from calling their victim and getting the same story.
- Myth:
Surely the Police would speak to Telstra about this?
The (horrible) truth: I’m not convinced it’s even occurred to them that it’s a bug, nor am I convinced that they’ve actually spoken to Telstra about it. But I am sending information to the Police about this, firstly to ascertain what has transpired, and secondly, (from a crime prevention perspective) to persuade them to be more on the front foot with Telstra on this issue.
The only sign of action by the authorities I can find is the British Financial Ombudsman Service has called for action by (British) telecoms companies to remedy the flaw in hanging up phone lines.

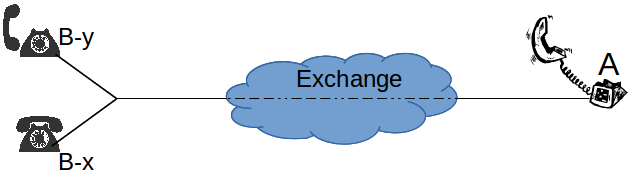
Land of the Long Held Call[1]
Land of the Long White Cloud[2]
Where is the bug?
It is in the telephone exchanges – specifically, the software running inside the exchange. This has to be fixed, either by the manufacturer of the telephone exchanges (Ericsson), or by someone changing a configuration setting. Telstra has to request this in either case, and it is likely to take 3-6 months to fix.
The official term for this is CSH (Called Subscriber Held) or A-party Release. I call it a nasty bug, but unfortunately, it is hard to convince Telstra that this needs fixing.
I have some questions
While researching anything like this, it is natural for questions to arise. Does anyone have information on anything below, or anything else? Please leave a comment.
Note that comments usually require approval before appearing, which I generally check three times a day … agree or disagree, I approve “anything” on-topic.
- Australia: Does anybody using Optus Cable (or other HFC services) experience the problem? Please do the test to find out.
- New Zealand: Did CSH apply on Crossbar or Step-by-Step exchanges (say, before 1980)?
- New Zealand – TelstraClear subscribers: Can someone do a test, to see if CSH applies to Telstra’s exchanges in NZ?
You are probably a TelstraClear subscriber if your telephone number begins with 9xx xxxx, and if your TelstraClear bill shows a line item for Telephone Line Rental or Monthly Charges. - Britain: There was a proposal to reduce the CSH hold period to 10 seconds. Was this implemented?
- U.S.: I don’t want to believe the movies too much 🙂 but they frequently show the B-party hanging up and the A-party receiving dial tone. Is that true?
- All countries: Please do the test. It’s for your benefit to be aware of the situation, as well as our curiosity 🙂
If you have information, please fill out a comment (note: DELAY before it appears, for most people).
Footnotes
- [1] CIA World Factbook / Wikimedia Commons / Public Domain
- [2] CIA World Factbook / Wikimedia Commons / Public Domain